Websites have become crucial platforms for sharing information and exchanging data. They often allow users to upload and download files in various formats. While this functionality adds dynamism and utility to websites, it can also introduce security vulnerabilities, especially when users do things they shouldn’t 😅. Let’s explore how to take precautions with PHP.
Comprehensive Precautions Against Security Vulnerabilities. Here are some common vulnerabilities and detailed precautions to mitigate them:
Preventing Unauthorized File Uploads
- User Authentication: Implement authentication mechanisms such as usernames and passwords to ensure only authorized users can upload files.
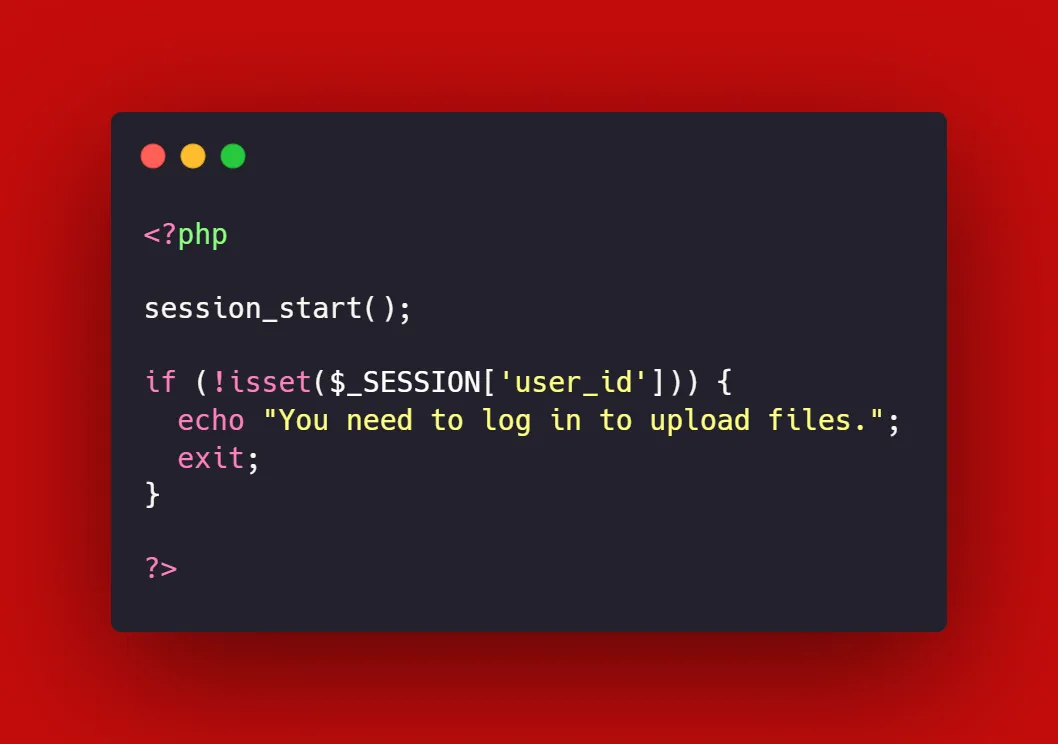
- Role-Based Access Control: Assign different file upload permissions to different user groups. For instance, administrators can be allowed to upload all file types, while regular users may only upload images and documents.
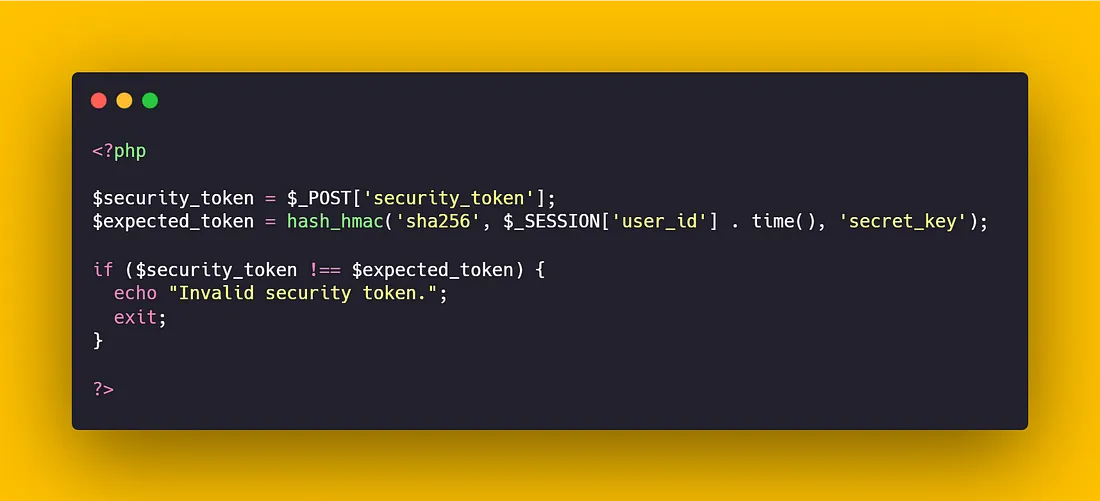
- Security Token Usage: Use randomly generated security tokens in form submissions and file upload requests to prevent fraudulent requests.
Preventing File Type Attacks
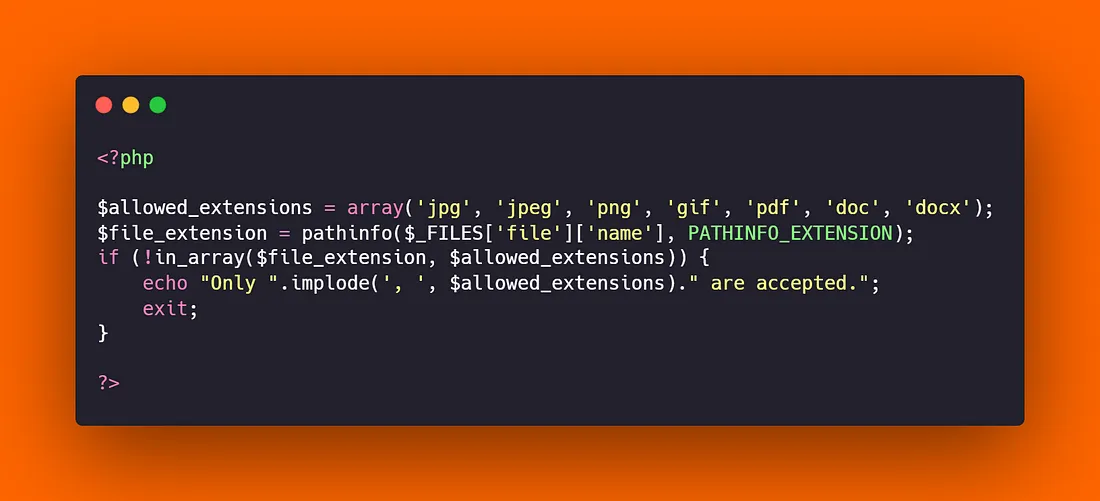
- Whitelist Usage: Permit only certain file types (e.g., images, documents, videos) to be uploaded. This helps prevent files containing malicious code from being uploaded.
- File Type Check: Verify the MIME type and file extension of the uploaded file. If either type does not match the allowed types, reject the upload.
- Content Type Checking: Sometimes the file content may contain malicious code even if the extension is correct. Use file analysis libraries to inspect the content of uploaded files.
Preventing File Size Attacks
- Maximum File Size Limitation: Ensure uploaded files do not exceed a certain size to prevent the depletion of server resources by malicious users.
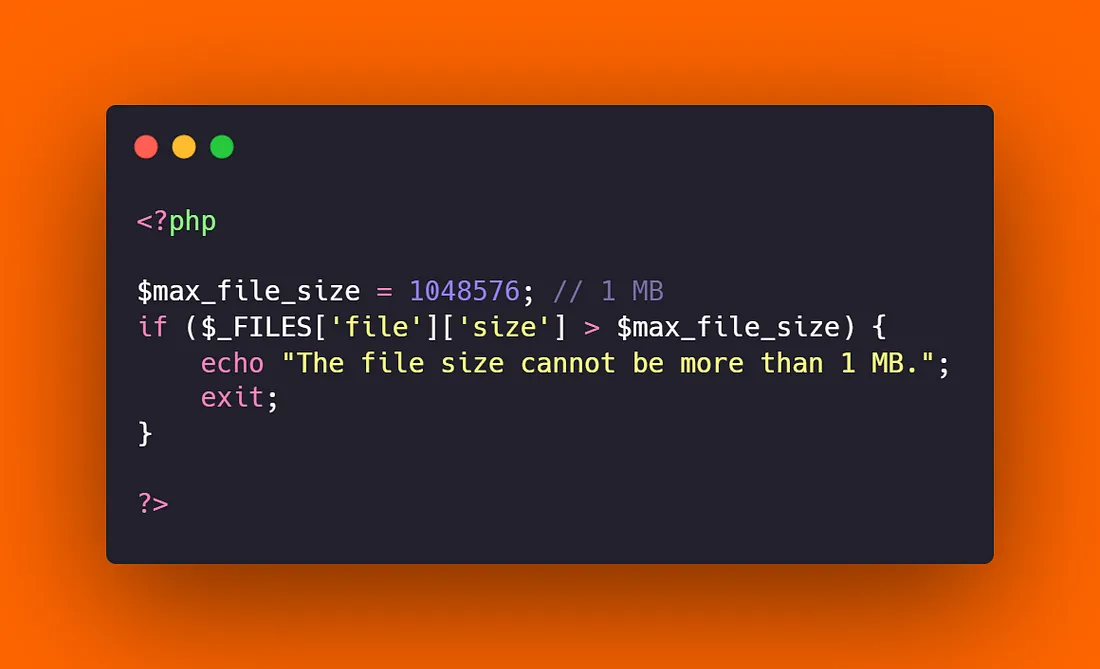
- Different File Size Limits: Set different maximum file size limits for various file types. For example, you can set limits like 2 MB for images, 5 MB for documents, and 100 MB for videos.
Preventing Path Attacks
- File Path Restriction: Ensure uploaded files are confined to a specific directory, preventing attackers from accessing the server file system and sensitive information.
- Using Virtual Paths: Serve uploaded files through virtual paths to hide the real file paths from attackers.
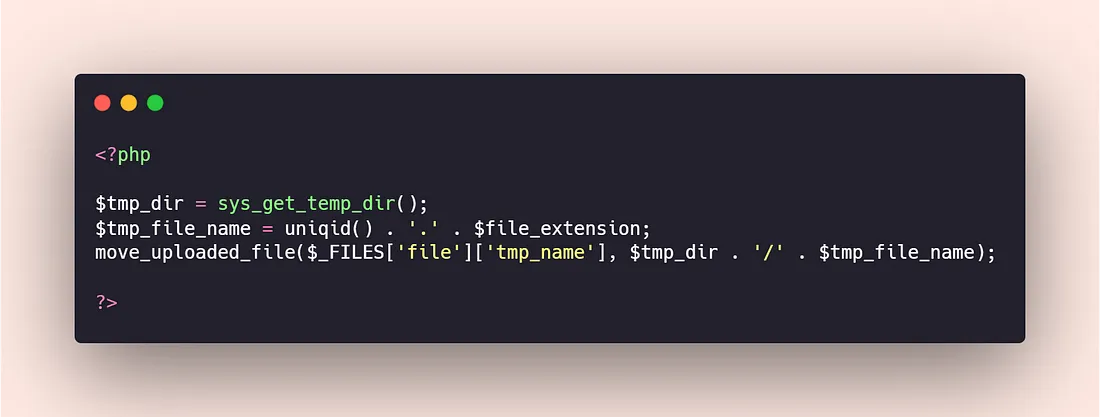
Ensuring File Verification
- Virus Scanning: Pass uploaded files through virus scanners to detect potential viruses and malware.
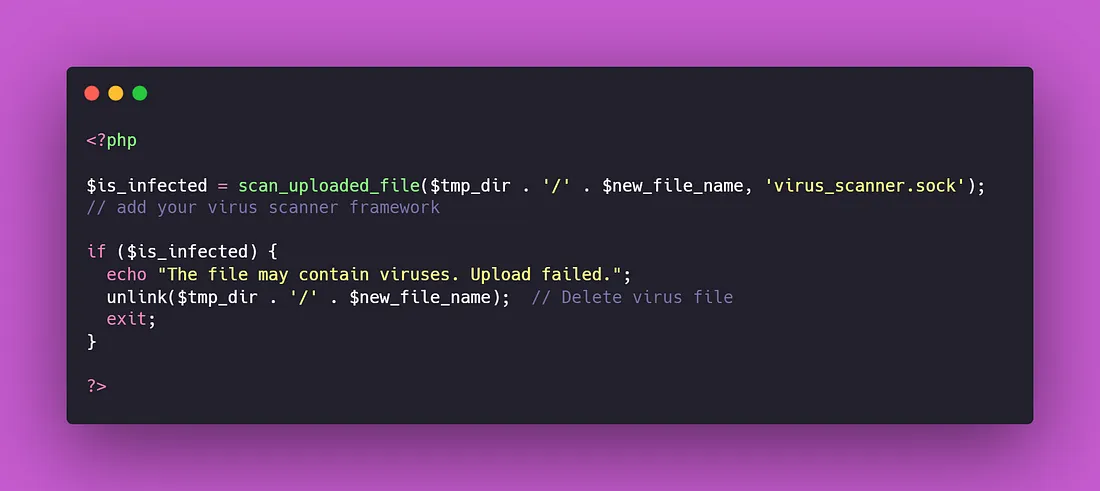
- File Integrity Check: Use hash algorithms such as MD5 or SHA256 to verify the integrity of the uploaded file.
- File Signature Verification: Allow only the upload of files signed with a digital signature and verify these signatures.
Remember, security is an ongoing process. Keeping your website updated, performing regular vulnerability scans, and staying informed about new security measures are all crucial steps.
Let’s ensure our websites remain safe and secure!
Fill-in the form below to reach out to us with your project👇




