In today’s interconnected digital landscape, Application Programming Interfaces (APIs) play a pivotal role in facilitating communication and data exchange between disparate systems and applications. However, with this increased connectivity comes a heightened risk of cyber threats. API Gateway, a key component in API management, acts as a mediator between clients and backend services, ensuring security, scalability, and reliability of API interactions.
Effective configuration of an API Gateway is crucial in fortifying the overall security posture of an organization. By implementing robust security measures at the gateway level, businesses can mitigate potential vulnerabilities and safeguard sensitive data from unauthorized access.
⚡Secure API Gateway Configuration:
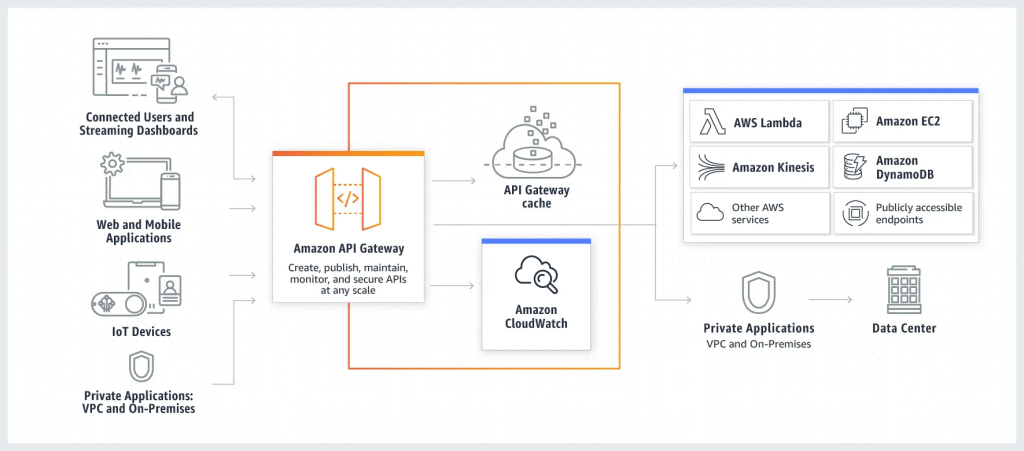
An API Gateway serves as the primary entry point for all API requests, offering a centralized location to enforce security and operational protocols. This essential component assists in various capacities, including:
- Enhanced Security: Acting as an additional layer of defense, the API Gateway shields against potential threats such as DDoS attacks, unauthorized access attempts, and misuse of APIs.
- Rate Limiting and Throttling: It regulates API usage by imposing limits on the frequency and volume of requests, ensuring equitable access and preventing overuse.
- Data Transformation and Validation: The API Gateway verifies incoming data to ensure compliance with predefined formats and standards, enhancing data integrity and consistency.
Implementing Secure API Gateway Configuration: When selecting an API Gateway provider for your application, several options are available, including Amazon API Gateway, Kong, and Google’s Apigee, among others. Each offers its unique features and benefits.
For instance, if you opt for Amazon Web Services (AWS), you can refer to their documentation for step-by-step guidance on setting up an API Gateway. However, additional configurations are necessary to optimize security and performance.
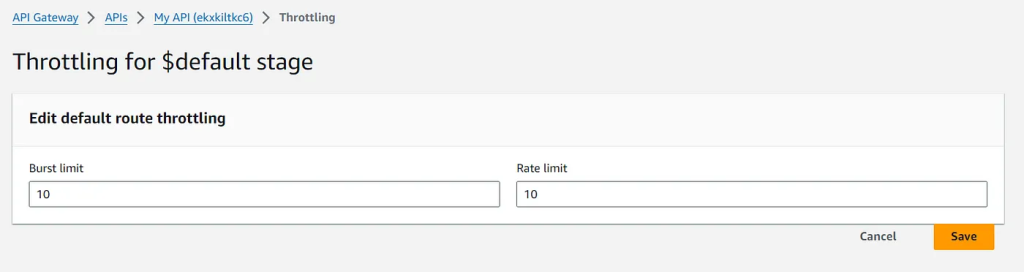
To initiate rate limiting in AWS, follow these steps:
- Access the AWS Management Console and navigate to the Amazon API Gateway section.
- Select the desired API and proceed to the Throttling settings located under the Protect tab.
- Within this section, specify the desired rate and burst limits to regulate the flow of incoming requests effectively.
By implementing these measures, you can bolster the security and efficiency of your API Gateway, ensuring seamless operation and safeguarding against potential threats.
To activate SSL/TLS, it’s crucial to link your API Gateway’s custom domain name with an SSL/TLS certificate managed through AWS Certificate Manager.
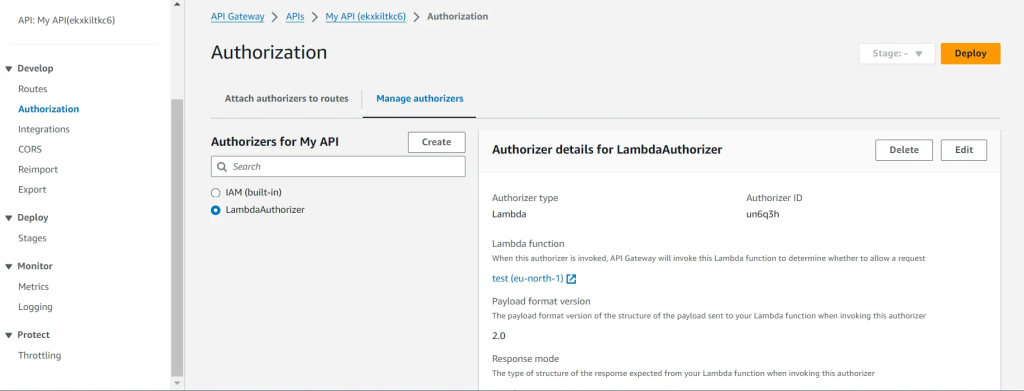
For implementing IP restrictions, leverage AWS Lambda authorizers to authenticate incoming request IP addresses. After deploying the function, designate it by generating a new authorizer within the API Gateway’s Authorization tab. Below is an example Lambda function in Python designed for IP restriction:
import json
def lambda_handler(event, context):
# Define allowed IP addresses
allowed_ips = ["192.0.2.0", "198.51.100.0"]
# Retrieve client IP address from the incoming event
client_ip = event['requestContext']['identity']['sourceIp']
# Validate if the client IP is within the allowed IP addresses
if client_ip in allowed_ips:
# If the IP is allowed, proceed with the request
return generate_policy("Allow", event['methodArn'])
else:
# If the IP is not allowed, deny the request
return generate_policy("Deny", event['methodArn'])
def generate_policy(effect, resource):
# Generate IAM policy for the Lambda authorizer
policy_document = {
"Version": "2012-10-17",
"Statement": [
{
"Action": "execute-api:Invoke",
"Effect": effect,
"Resource": resource
}
]
}
# Return policy document
return {
"principalId": "user",
"policyDocument": policy_document
}
This Lambda function validates incoming requests against a predefined list of allowed IP addresses, granting access only to those within the specified range. Integrate this function with AWS Lambda authorizers to enforce IP restrictions effectively within your API Gateway.
⚡ Encrypt Sensitive Data in Transit and at Rest
Securing sensitive data during transmission and storage is a fundamental aspect of maintaining data integrity and confidentiality, thwarting unauthorized access and potential breaches. Encryption serves as a cornerstone in achieving this security objective, with encryption in transit safeguarding data during its movement between clients and servers, and encryption at rest ensuring its protection when stored on disk or within databases.
Implementing Encryption in Transit: When utilizing your own web server, setting up and managing SSL/TLS certificates is imperative. Initially, you must procure certificates from reputable Certificate Authorities (CAs) such as Let’s Encrypt, DigiCert, or GoDaddy. Subsequently, configure your server to utilize these certificates. For instance, here’s a guide on configuring SSL with Nginx:
- Locate and modify the Nginx configuration file, typically found at paths like /etc/nginx/nginx.conf or /etc/nginx/sites-available/your_site.
- Within the server block of the configuration file, incorporate SSL settings. An example configuration snippet is provided below:
server {
listen 443 ssl;
server_name your_domain.com;
ssl_certificate /path/to/your_ssl_certificate.crt;
ssl_certificate_key /path/to/your_ssl_certificate_key.key;
# Other SSL configurations (e.g., SSL protocols, ciphers, etc.) can be added here
}In this snippet:
listen 443 ssl;directs Nginx to listen for HTTPS connections on port 443 and enables SSL/TLS encryption.server_name your_domain.com;specifies the domain name associated with the SSL certificate.ssl_certificateandssl_certificate_keydirectives point to the paths of your SSL certificate and corresponding private key files, respectively.
By following these steps and customizing the configuration to suit your environment, you can effectively implement encryption in transit, fortifying the security of data exchanged between clients and your web server.
Fill-in the form below to reach out to us with your project👇




